
For your reading pleasure, I have attached several articles on the internet of things (which I call “The Internet of Everything”) and an article on a cyber-attack on the cloud; which used “the internet of things” as a platform for the attack.
I miss my old “birdcage” refrigerator but, when I am in the grocery store, (Safeway) I sure like looking inside of my new refrigerator to determine just how old the milk is or if I am out of eggs. It was quite the revelation to me that my new refrigerator could be used by “evil doers” in a denial-of-service attack on the internet. I never knew that so many of my devices in my home had security passwords. It never occurred to me that I could, or should, change them or that my house and personal items were at risk.
To my knowledge, the recent attack was the first such attack using internet connected devices or THE INTERNET OF THINGS.
The internet of things (IoT) allows objects to be sensed and/or controlled remotely across existing network infrastructure, creating opportunities for more direct integration of the physical world into computer-based systems, and resulting in improved efficiency, accuracy, and economic benefit. Alexa from Amazon is the most recent addition
In my opinion, a major reason for the IoT vulnerability to cyberattacks was that the public (and many of our cyber professionals) did not understand that every device connected to the internet has a security password and that those passwords needed to be managed.
I have seen an argument that this attack could have been avoided if there had been an oversight body creating security standards for IoT,
There is no singular overriding body responsible for creating a minimum-security level to limit access by the wrong people to our microwave ovens.
Having such a body probably would not be successful for several reasons. If we created such an organization, then it would probably be more difficult for small and creative companies to make anything. Most oversight bodies would not stay current with the changing technology and then our tech industry would be saddled with mandates for outdated security technology in all of the devices. As a result, my internet espresso maker could cost $1200 instead of $200. and still would make bad Americanos when I asked Seri to start it up in the morning.
Finance Companies such as banks and credit card companies, medical organizations, phone companies and computer companies all have significant financial incentives to create secure devices. They all work diligently with the public to make sure that everyone is aware of a need for quality passwords and that the passwords are aggressively managed. And yet even they have had significant problems keeping their information and systems secure from the internet mischief makers.
(I digress here but….) An axiom in cyber security is that there is no system that is 100% secure unless it is not attached in any way to the internet. An additional reason for private industry diligence is that the US Government severely punishes the victim when there is a breach… (not only did the data go away, not only did sales drop because of a reputation problem, customers sue them and then, as a cherry on the top of the Sunday; rather than helping the victim, the U.S. Government then fines the victims. I agree that every organization should be very diligent with their customer’s data. However, the government punishing the victim seems to be overkill in many situations
Most of the people who I know who have spent any time thinking about purchasing self-driving automobiles have commented to me of a concern that hackers could take over their car. In discussion with them on this issue their major concern seems to be that the bad guys will be driving the cars off of Golden Gate Bridge. There is (and should be) far more concern over the loss of control of a car than loss of control of a pizza oven but to me it is all really part of the same problem.
So… my first question was “Is there a locus or specific place where we can plug in some type of security to help stop the mischief?”
Looking for insight I charged down to Best Buy and asked one of their Geek Squad folks if there was any technology or way to limit outside access or control to my internet connected electronic toothbrush?
Eric The Geek said “No”. It appears that there is no Ronco IoT security hardware device for only $19.99 and… if you call in the next two minutes… you can have TWO Ronco Internet security devices which will protect you and your loved ones from IoT mischief.
Eric said that believed that the best opportunity for such security has to do with the individual routers in the homes. As an aside he also said that since my dental floss dispenser was not connected to the internet that I would not have to worry about one of my teeth being yanked out by an evil doer from Nigeria who was trying to get that pesky $25M out of the country.
I was surprised that he did not tell me to go home and change all of the passwords on my IoT devices from “Password” to “FlyMeToTheMoon#1”.
On the bright side, I did come out of Best Buy with a brand new three-year software internet security program for my new computer. It only cost me $49.95 discounted to $9.95 because I was also purchasing a new internet connected cat sandbox.
Some the follow up questions and issues:
1. Should there be an oversight body for all devices that will be responsible for creating a minimum standard for security for all of the internet connected heating systems in the world? (The NSA will still want back-door access to all of the data from your garage opener). If there is an oversight body and it creates a minimum-security program or level will it be enough to keep the evil doers out of my kitchen? I do not believe that there will ever be one oversight body.
2. Who will go on Shark Tank with the next device (Ronco??) to help you create some sort of security for all of the devices in your home? This seems like a great opportunity for someone or some company.
3. Perhaps the cable operators (those who supply the infrastructure of the connectivity) who should be held responsible for identifying viruses as they go across the cables and stop them. This is where the NSA gets all of its data anyway, why not use it for good instead of just collecting information for governmental organizations?
4. Will I ever be able to look at my internet connected microwave pizza oven without wondering if it is actually a drone for a hacker in Uzbekistan? Will the evil doers burn my Pizza instead of me burning it? Or worse… Will they undercook things? Will a hacker drive my car (in two years Uber’s car) off of the Golden Gate Bridge? Will I actually be in the car when they drive off with it?
5. Will the evil-doers now open my garage door and take my X mas stuff? There is really a serious question of personal security that will become more difficult and complex as more of the bad guys find out how to easily get into some homes and office buildings.
6. Will the Government take over my sprinkler systems and stop me from wasting water? The underlying question of how much can (or will) the Federal State and Local Government eventually want to know or have access to will be an interesting battleground for the next 15 years.
7. Who has the information concerning where are all of the IoT devices? Knowing where the devices are will allow the evil doers to attack the weakest links. I believe that the bad guys first hacked the companies who sell the devices in order to find out where those devices were. Should you sign up for a warranty if that information will result in telling the mischief makers where you are and how you are connected?
8. Just how safe is the cloud? this was a denial of service attack but can the evil doers use my internet connected fireplace to hack the cloud? If they do will it rain?
9. The IoT security problems has profound privacy issues. What if the miscreants leak my information to WikiLeaks about the fact that I keep my peanut butter in the refrigerator and my butter on the counter? A recent news story was about police asking for information from Amazon about what Alexa heard because she was in the same room as a suspected killer. Alexa never really goes off. She just sits silently listening to everything waiting for the magic question “Alexa is my pizza oven infested with a virus from Tajikistan?” Should Alexa be in the other room when mom and dad are napping?
As they say… Inquiring minds want to know.
There is an amazing amount of mischief that can be created if we do not have secure devices. There are also many questions and issues which surround the IoT.
Think about it.
And perhaps you should do as I did and un-plug your internet connected litter robot until you know it will only be used by your cat for its original purpose.
Bill Zachry
The Internet of things, stylised Internet of Things (IoT), is the internetworking of physical devices, vehicles (also referred to as “connected devices” and “smart devices“), buildings and other items—embedded with electronics, software, sensors, actuators, and network connectivity that enable these objects to collect and exchange data.[1][2][3]
In 2013 the Global Standards Initiative on Internet of Things (IoT-GSI) defined the IoT as “the infrastructure of the information society.”[3] The IoT allows objects to be sensed and/or controlled remotely across existing network infrastructure,[4] creating opportunities for more direct integration of the physical world into computer-based systems, and resulting in improved efficiency, accuracy and economic benefit.[5][6][7][8][9][10] When IoT is augmented with sensors and actuators, the technology becomes an instance of the more general class of cyber-physical systems, which also encompasses technologies such as smart grids, smart homes, intelligent transportation and smart cities. Each thing is uniquely identifiable through its embedded computing system but is able to interoperate within the existing Internet infrastructure. Experts estimate that the IoT will consist of almost 50 billion objects by 2020.[11]
Typically, IoT is expected to offer advanced connectivity of devices, systems, and services that goes beyond machine-to-machine (M2M) communications and covers a variety of protocols, domains, and applications.[12] The interconnection of these embedded devices (including smart objects), is expected to usher in automation in nearly all fields, while also enabling advanced applications like a smart grid,[13] and expanding to the areas such as smart cities.[14][15]
“Things,” in the IoT sense, can refer to a wide variety of devices such as heart monitoring implants, biochip transponders on farm animals, electric clams in coastal waters,[16] automobiles with built-in sensors, DNA analysis devices for environmental/food/pathogen monitoring[17] or field operation devices that assist firefighters in search and rescueoperations.[18] Legal scholars suggest to look at “Things” as an “inextricable mixture of hardware, software, data and service”.[19] These devices collect useful data with the help of various existing technologies and then autonomously flow the data between other devices.[20] Current market examples include home automation (also known as smart home devices) such as the control and automation of lighting, heating (like smart thermostat), ventilation, air conditioning (HVAC) systems, and appliances such as washer/dryers, ovens or refrigerators/freezers that use Wi-Fi for remote monitoring.
As well as the expansion of Internet-connected automation into a plethora of new application areas, IoT is also expected to generate large amounts of data from diverse locations, with the consequent necessity for quick aggregation of the data, and an increase in the need to index, store, and process such data more effectively. IoT is one of the platforms of today’s Smart City, and Smart Energy Management Systems.[21][22]
Hacked Cameras, DVRs Powered Today’s Massive Internet Outage
A massive and sustained Internet attack that has caused outages and network congestion today for a large number of Web sites was launched with the help of hacked “Internet of Things” (IoT) devices, such as CCTV video cameras and digital video recorders, new data suggests.
Earlier today cyber criminals began training their attack cannons on Dyn, an Internet infrastructure company that provides critical technology services to some of the Internet’s top destinations. The attack began creating problems for Internet users reaching an array of sites, including Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix.
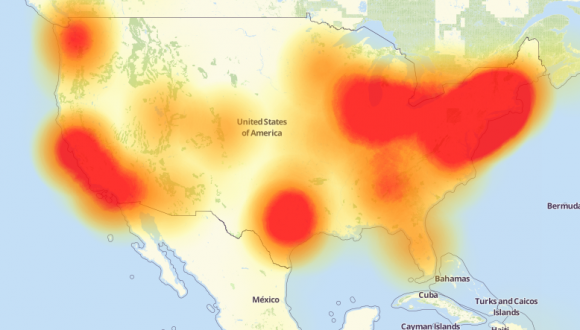
A depiction of the outages caused by today’s attacks on Dyn, an Internet infrastructure company. Source: Downdetector.com.
At first, it was unclear who or what was behind the attack on Dyn. But over the past few hours, at least one computer security firm has come out saying the attack involved Mirai, the same malware strain that was used in the record 620 Gpbs attack on my site last month. At the end September 2016, the hacker responsible for creating the Mirai malware released the source code for it, effectively letting anyone build their own attack army using Mirai.
Mirai scours the Web for IoT devices protected by little more than factory-default usernames and passwords, and then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors or users.
According to researchers at security firm Flashpoint, today’s attack was launched at least in part by a Mirai-based botnet. Allison Nixon, director of research at Flashpoint, said the botnet used in today’s ongoing attack is built on the backs of hacked IoT devices — mainly compromised digital video recorders (DVRs) and IP cameras made by a Chinese hi-tech company called XiongMai Technologies. The components that XiongMai makes are sold downstream to vendors who then use it in their own products.
“It’s remarkable that virtually an entire company’s product line has just been turned into a botnet that is now attacking the United States,” Nixon said, noting that Flashpoint hasn’t ruled out the possibility of multiple botnets being involved in the attack on Dyn.
“At least one Mirai [control server] issued an attack command to hit Dyn,” Nixon said. “Some people are theorizing that there were multiple botnets involved here. What we can say is that we’ve seen a Mirai botnet participating in the attack.”
As I noted earlier this month in Europe to Push New Security Rules Amid IoT Mess, many of these products from XiongMai and other makers of inexpensive, mass-produced IoT devices are essentially unfixable, and will remain a danger to others unless and until they are completely unplugged from the Internet.
That’s because while many of these devices allow users to change the default usernames and passwords on a Web-based administration panel that ships with the products, those machines can still be reached via more obscure, less user-friendly communications services called “Telnet” and “SSH.”
Telnet and SSH are command-line, text-based interfaces that are typically accessed via a command prompt (e.g., in Microsoft Windows, a user could click Start, and in the search box type “cmd.exe” to launch a command prompt, and then type “telnet” to reach a username and password prompt at the target host).
“The issue with these particular devices is that a user cannot feasibly change this password,” Flashpoint’s Zach Wikholm told KrebsOnSecurity. “The password is hardcoded into the firmware, and the tools necessary to disable it are not present.
“The issue with these particular devices is that a user cannot feasibly change this password,” Flashpoint’s Zach Wikholm told KrebsOnSecurity. “The password is hardcoded into the firmware, and the tools necessary to disable it are not present. Even worse, the web interface is not aware that these credentials even exist.”
Flashpoint’s researchers said they scanned the Internet on Oct. 6 for systems that showed signs of running the vulnerable hardware, and found more than 515,000 of them were vulnerable to the flaws they discovered.
“I truly think this IoT infrastructure is very dangerous on the whole and does deserve attention from anyone who can take action,” Flashpoint’s Nixon said.
It’s unclear what it will take to get a handle on the security problems introduced by millions of insecure IoT devices that are ripe for being abused in these sorts of assaults.
As I noted in The Democratization of Censorship, to address the threat from the mass-proliferation of hardware devices such as Internet routers, DVRs and IP cameras that ship with default-insecure settings, we probably need an industry security association, with published standards that all members adhere to and are audited against periodically.
The wholesalers and retailers of these devices might then be encouraged to shift their focus toward buying and promoting connected devices which have this industry security association seal of approval. Consumers also would need to be educated to look for that seal of approval. Something like Underwriters Laboratories (UL), but for the Internet, perhaps.
Until then, these insecure IoT devices are going to stick around like a bad rash — unless and until there is a major, global effort to recall and remove vulnerable systems from the Internet. In my humble opinion, this global cleanup effort should be funded mainly by the companies that are dumping these cheap, poorly-secured hardware devices onto the market in an apparent bid to own the market. Well, they should be made to own the cleanup efforts as well.
Devices infected with Mirai are instructed to scour the Internet for IoT devices protected by more than 60 default usernames and passwords. The entire list of those passwords — and my best approximation of which firms are responsible for producing those hardware devices — can be found at my story, Who Makes the IoT Things Under Attack.
Update 10:30 a.m., Oct. 22: Corrected attribution on outage graphic.
Tags: Allison Nixon, Dyn, Flashpoint, internet of things, mirai, Underwriters Laboratories, XiongMai Technologies, Zach Wikholm
Who Makes the IoT Things Under Attack?
As KrebsOnSecurity observed over the weekend, the source code that powers the “Internet of Things” (IoT) botnet responsible for launching the historically large distributed denial-of-service (DDoS) attack against KrebsOnSecurity last month has been publicly released. Here’s a look at which devices are being targeted by this malware.
The malware, dubbed “Mirai,” spreads to vulnerable devices by continuously scanning the Internet for IoT systems protected by factory default usernames and passwords. Many readers have asked for more information about which devices and hardware makers were being targeted. As it happens, this is fairly easy to tell just from looking at the list of usernames and passwords included in the Mirai source code.
In all, there are 68 username and password pairs in the botnet source code. However, many of those are generic and used by dozens of products, including routers, security cameras, printers and digital video recorder (DVRs).
I examined the less generic credential pairs and tried to match each with a IoT device maker and device type. As we can see from the spreadsheet above (also available in CSV and PDFformats), most of the devices are network-based cameras, with a handful of Internet routers, DVRs and even printers sprinkled in.
I don’t claim to have special knowledge of each match, and welcome corrections if any of these are in error. Mainly, I turned to Google to determine which hardware makers used which credential pairs, but in some cases this wasn’t obvious or easy.
Which is part of the problem, says Will Dormann, senior vulnerability analyst at the CERT Coordination Center (CERT/CC).
“Even when users are interested in and looking for this information, the vendor doesn’t always make it easy,” Dormann said.
Dormann said instead of hard-coding credentials or setting default usernames and passwords that many users will never change, hardware makers should require users to pick a strong password when setting up the device.
Indeed, according to this post from video surveillance forum IPVM, several IoT device makers — including Hikvision, Samsung, and Panasonic — have begun to require unique passwords by default, with most forcing a mix of upper and lowercase letters, numbers, and special characters.
“As long as the password can’t be reversed — for example, an algorithm based off of a discoverable tidbit of information — that would be a reasonable level of security.” Dormann said.
Some readers have asked how these various IoT devices could be exposed if users have configured them to operate behind wired or wireless routers. After all, these readers note, most consumer routers assign each device inside the user’s home network so-called Network Address Translation (NAT) addresses that cannot be directly reached from the Internet.
But as several readers already commented in my previous story on the Mirai source code leak, many IoT devices will use a technology called Universal Plug and Play (UPnP) that will automatically open specific virtual portholes or “ports,” essentially poking a hole in the router’s shield for that device that allows it to be communicated with from the wider Internet. Anyone looking for an easy way to tell whether any of network ports may be open and listening for incoming external connections could do worse than to run Steve Gibson‘s “Shields Up” UPnP exposure test.
HELP! I NEVER CHANGED THE DEFAULT PASSWORD!
Regardless of whether your device is listed above, if you own a wired or wireless router, IP camera or other device that has a Web interface and you haven’t yet changed the factory default credentials, your system may already be part of an IoT botnet. Unfortunately, there is no simple way to tell one way or the other whether it has been compromised.
However, the solution to eliminating and preventing infections from this malware isn’t super difficult. Mirai is loaded into memory, which means it gets wiped once the infected device is disconnected from its power source.
But as I noted in Saturday’s story, there is so much constant scanning going on for vulnerable systems that IoT devices with default credentials can be re-infected within minutes of a reboot. Only changing the default password protects them from rapidly being reinfected on reboot.
My advice for those running devices with the default credentials? First off, make sure you know how to access the device’s administration panel. If you’re unsure how to reach the administration panel, a quick search online for the make and model of your device should reveal an address and default credential pair that can be typed or pasted into a Web browser.
If possible, reset the device to the factory-default settings. This should ensure that if any malware has been uploaded to the device that it will be wiped permanently. Most devices have a small, recessed button that needs to be pressed and held down for a several seconds while powered on to reset the thing back to the factory default settings.
When the device comes back online, quickly fire up a Web browser, navigate to the administration panel, enter the default credentials, and then change the default password to something stronger and more memorable. I hope it goes without saying that any passwords remotely resembling the default passwords noted in the image above are horrible passwords. Here’s some advice on picking better ones.
Unfortunately, many of these devices also require periodic software or “firmware” updates to fix previously unknown security vulnerabilities that the vendor discovers or that are reported to the hardware maker post-production. However, relatively few hardware makers do a good job of making this process simple and easy for users, let alone alerting customers to the availability of firmware updates.
“When it comes to software updates, automatic updates are good,” Dormann said. “Simple updates that notify the user and require intervention are okay. Updates that require the user to dig around to find and install manually are next to worthless. Devices that don’t have updates at all are completely worthless. And that can be applied to traditional computing as well. It’s just that with IoT, you likely have even-less-technical users at the helm.”
Only after fixing any problems related to default credentials should readers consider checking for firmware updates. Some hardware makers include the ability to check for updates through a Web-based administration panel (like the one used to change the device’s default password), while others may only allow firmware updates manually via downloads from the manufacturer’s site.
Firmware updates can be tricky to install, because if you fail follow the manufacturer’s instructions to the letter you may end up with little more than an oversized paperweight. So if you decide to go ahead with any firmware updates, please do so carefully and deliberately.
BUT WAIT, THERE’S MORE
Several readers have pointed out that while advising IoT users to change the password via the device’s Web interface is a nice security precaution, it may or may not address the fundamental threat. That’s because Mirai spreads via communications services called “telnet” and “SSH,” which are command-line, text-based interfaces that are typically accessed via a command prompt (e.g., in Microsoft Windows, a user could click Start, and in the search box type “cmd.exe” to launch a command prompt, and then type “telnet” <IP address> to reach a username and password prompt at the target host).
The trouble is, even if one changes the password on the device’s Web interface, the same default credentials may still allow remote users to log in to the device using telnet and/or SSH.
Brian Karas, a business analyst with IPVM — a subscription-based news, testing and training site for the video surveillance industry — said in his experience often times IP camera users can change whatever settings they want in the device’s Web interface, but that’s no guarantee the changes will affect how the device can be accessed via Telnet or SSH.
“The problem is there’s no hard and fast rule,” Karas said. “What often happens is Telnet and SSH are an operating system-level login, and the [Web interface] tends to be more of an application level login. Sometimes changing a password on one changes the password on the other, but more often the Web [interface] is completely different, and changing the password there may not change the underlying password” needed to access the device remotely via SSH and Telnet, he said.
Case in point: In February 2016 I published This is Why People Fear the Internet of Things, which examined a whole slew of IP cameras sold by Chinese Web camera giant Foscam that — by default — included a feature which would quietly phone home to a vast peer-to-peer (P2P) network run by the company. As I explained in that piece, while the Web interface for those P2P cameras included a setting allowing users to disable the P2P traffic, disabling that option didn’t actually do anything to stop the device from seeking out other Foscam P2P cameras online.
Interestingly, Karas said he’s been pressing Dahua — whose IoT devices are heavily represented in the above default password list — to tell him how many of their devices are vulnerable. Karas said Dahua told him that although the company’s newest models didn’t have this problem, the company was preparing to launch a trade-in program for customers with default-insecure devices.
“They didn’t give me a straight answer on this one, but that that tells me is they have a whole bunch of devices that may not be firmware updatable, which means they can’t make those devices more secure without swapping out the underlying hardware.”


